TAKE NOTE (Insights and Emerging Technology)
The CODY bot, a tool used to streamline procurement processes at the General Services Administration, is now ready for use across the federal landscape after three years of build-out.
CODY aggregates prerequisite data into a checklist, according to GSA officials familiar with the tool, enabling staffers to see if a vendor has met all representation requirements — ensuring there is no active federal debt against a vendor, and no exclusionary or responsibility cautions to trigger notifications.
The agency primarily tracks how many hours the bot saves in a year rather than the costs saved, according to one of the officials. GSA Administrator Stephen Ehikian posted on X that the bot’s completion resulted in the cancellation of a $423,000 contract.
The bot was built in-house, an agency official said. Work began on CODY — a nod to the Irish origins of the name meaning “helpful one” — in 2022.
GSA is sharing the automation code for CODY with other agencies that use Robotic Process Automation programs and “similar RPA technology,” sources familiar with the project said.
Automation software from UiPath that mimics actions that an individual would perform on a computer was used to help build CODY, a GSA official said. Another agency source said that the CODY team built the tool — in part — within side applications like Python, Adobe and some Google scripting.
Sources familiar with the project confirmed that the tool was first showcased during GSA’s first Friday demo day, a new internal demonstration program at the agency where offices can show how they’re using software and technology.
The inaugural demo day followed an announcement from Technology Transformation Services Director Thomas Shedd that TTS would face a 50% reduction in staff.
Before demo days were announced, the GSA would only take on work that was statutorily required and aligned with Trump administration priorities. Last week, GSA announced internally that there would be more staff cuts to TTS, including to the Office of Regulatory and Oversight Systems program.
Interested in learning more about RPA? Download our FREE White Paper on “Embracing the Future of Work”
UNDER DEVELOPMENT (Insights for Developers)
CMMC Compliance and Your Business
Intro
Just like we do with our other blogs, we’re going to take a practical, plain-English dive into something critical for businesses operating in or aspiring to enter the defense sector, the Cybersecurity Maturity Model Certification, or CMMC.
This isn’t going to be another jargon-heavy compliance lecture. Instead, I’ll take you step-by-step through what CMMC is, why it matters, and what your business actually needs to do to comply—all in a way that makes sense. I know first hand how this works as IT Partners has passed our CMMC 2.0 audit a few months back.
Let’s start with the why.
The Department of Defense (DoD) created CMMC to raise the bar on cybersecurity across the Defense Industrial Base (DIB). We’re talking about hundreds of thousands of contractors and subcontractors who may have access to Federal Contract Information (FCI) or Controlled Unclassified Information (CUI). In the past, adherence to security requirements—like those outlined in NIST SP 800-171—was largely self-attested. Predictably, this led to gaps and, unfortunately, breaches.
With CMMC, the DoD is saying: “Enough. You have to prove you’re protecting sensitive data if you want to keep doing business with us.”
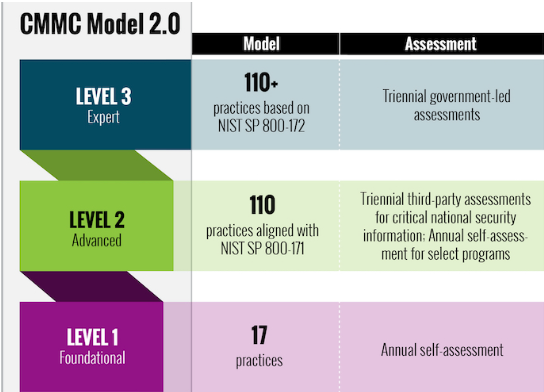
CMMC 2.0 is the refined version. The original framework had five levels, but the DoD heard industry feedback and simplified it to three more streamlined tiers:
Level 1: Foundational
This is your entry-level tier. It includes 17 basic cyber hygiene practices that align with FAR 52.204-21, like using antivirus software, enforcing password complexity, and limiting access to information. Think of this as the basics everyone should be doing anyway. If you’re handling only FCI, this is your floor.
Level 2: Advanced
This is where things get serious. Level 2 aligns with all 110 practices from NIST SP 800-171. If your company deals with CUI—and most defense contractors do—you’ll likely need to certify at this level. Some programs allow for self-assessment, but many require a third-party C3PAO (Certified Third-Party Assessment Organization) audit. This was the level here at IT Partners we passed.
Level 3: Expert
This tier incorporates additional requirements from NIST SP 800-172. It’s designed for organizations supporting critical programs where the threat of Advanced Persistent Threats (APTs) is high. This is not for the faint of heart—it requires continuous monitoring, advanced threat detection, and government-led assessments.
– Dig Deeper –
The Basics of NIST 800-171
Q&A (Post your questions and get the answers you need)

Q. What is CMMC 2.0, and how does it relate to NIST 800-171 and other cybersecurity frameworks?
A. CMMC 2.0, or the Cybersecurity Maturity Model Certification version 2.0, is a unified standard developed by the Department of Defense (DoD) to ensure that contractors and subcontractors in the Defense Industrial Base (DIB) are adequately protecting sensitive unclassified information, particularly Controlled Unclassified Information (CUI) and Federal Contract Information (FCI). It streamlines and enhances the original CMMC model by reducing the number of compliance levels from five to three, aligning more directly with existing federal standards, and introducing more flexibility in assessment methods.
What makes CMMC 2.0 particularly significant is its tighter integration with the NIST framework. Rather than layering a new set of requirements on top of existing ones, the DoD is now leaning into NIST SP 800-171 as the authoritative baseline for Level 2, reducing ambiguity and aligning with already-established best practices. This means that companies preparing for CMMC compliance should continue implementing and documenting NIST 800-171 controls and pay close attention to the assessment guides published by NIST. Organizations that have already invested in NIST-based security programs will find themselves better positioned to meet CMMC 2.0 requirements.

The three levels in CMMC 2.0 are as follows:
- Level 1 (Foundational) applies to companies handling FCI and requires annual self-assessments based on 17 basic cybersecurity practices drawn from FAR 52.204-21.
- Level 2 (Advanced) is designed for companies that handle CUI and aligns directly with NIST SP 800-171’s 110 security controls. Depending on the sensitivity of the information involved, assessments may be either self-assessed or conducted by a certified third party (C3PAO).
- Level 3 (Expert) is still in development but will be based on a subset of NIST SP 800-172 and involve government-led assessments, reflecting the highest standards of cybersecurity for the most sensitive DoD programs.
Cheers!